Container Security: Network Visibility
Network Inspection + Container Firewall for unmatched visibility
You can’t secure what you can’t see. Deep network visibility is the most critical part of runtime container runtime security. In traditional perimeter-based security, administrators deploy firewalls to quarantine or block attacks before they reach the workload. Inspecting container network traffic reveals how an application communicates with other applications and it’s the only place to stop attacks before they reach the application or workload. It’s also the last chance to prevent data breaches by exploited applications which send data out over the network. Proper network controls will limit the ‘blast radius’ of an attack.
NeuVector enables you to see all the traffic on your network.
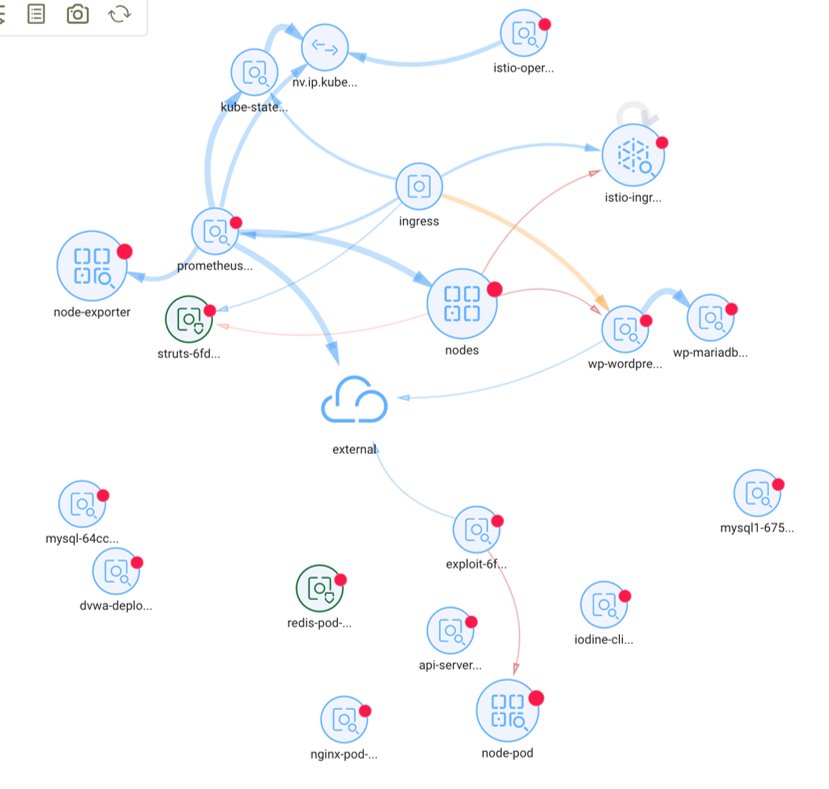
NeuVector goes beyond static diagrams which are based on the inspection of the deployment manifests of container services and the open ports or syscalls during run-time, to deliver real-time analysis of true network traffic that is being filtered and inspected, rather than trying to guess network connections. NeuVector’s patented technology is the only solution to deliver production-grade container security that enables security teams to:
- Perform Deep Packet Inspection (DPI):NeuVector applies DPI to identify attacks, detect sensitive data, or verify application access to further reduce the attack surface. Only network layer analysis enables security to detect and verify the allowed protocols, helping security teams enforce business policy.
- Deliver real-time protection with the industry’s only Container Firewall: NeuVector’s container firewall provides inspection, segmentation, and protection of all traffic into and out of a container. This includes container to container traffic as well as ingress from external sources to containers, and egress from containers to external applications and the internet. Our Layer 7 container firewall protects your applications from internal application level attacks such as DDoS and DNS.
- Monitor ‘East-west’ and ‘North-south’ container traffic: Microservices and containers dramatically increase internal East-West traffic in a data center. Without application-aware container network security, an attacker can exploit containers once inside a data center. NeuVector detects and displays real-time connection info for all container traffic, internal, ingress and egress.
- Capture Packets for Debugging and Threat Investigation: NeuVector makes it easy to view summary connection data and drill down into actual packet details for each container, even as they scale up and down. When a threat is detected, NeuVector will automatically capture and display the packet info, making it easy to investigate.
NeuVector: Full Lifecycle Cloud Container Security Platform
NeuVector is the only 100% open source, Zero Trust container security platform. Continuously scan throughout the container lifecycle, remove security roadblocks, & bake in security policies at the start to maximize developer agility. Get started on kubernetes security by getting NeuVector on GitHub.
Related Articles
Jun 28th, 2023
SUSECON Digital 2023: SUSE powers RISE with SAP
Apr 18th, 2025
On-Premise AI: Control Your Data, Own Your Future
May 09th, 2025