Deploying Citrix Ingress Controller via the Rancher Catalog
Citrix Ingress Controller is an emerging enterprise-grade ingress controller for load balancing microservices in the Kubernetes environment. It provides advanced load balancing, rewrite/responder policy support, advanced content routing, SSL/TLS support, TCP/UDP protocol support, Canary deployment support and much more.
In this article, we will discuss different deployment modes for Citrix Ingress Controller and deploy it via the Rancher catalog.
You can deploy Citrix Ingress Controller in the following modes:
-
As a standalone pod. This mode is used when managing Citrix ADC’s flavors, such as MPX or VPX, that are outside the Kubernetes cluster.
-
As a sidecar in a pod along with the Citrix ADC CPX in the same pod. The controller is only responsible for the Citrix ADC CPX that resides in the same pod.
Citrix has partnered with Rancher to collaborate and simplify deploying Citrix Ingress Controller with Rancher catalog. You can find the Citrix Ingress Controller catalog in the default library of the Rancher catalog.

Citrix Ingress Controller charts in the default library of Rancher catalog
Setting Up Citrix Ingress Controller
Deploying Citrix Ingress Controller as sidecar
- Select citrix-k8s-cpx-ingress-controller Rancher catalog for CIC running as sidecar with Citrix ADC CPX. You can customize the Citrix Ingress Controller’s pod-name and pod-namespace.
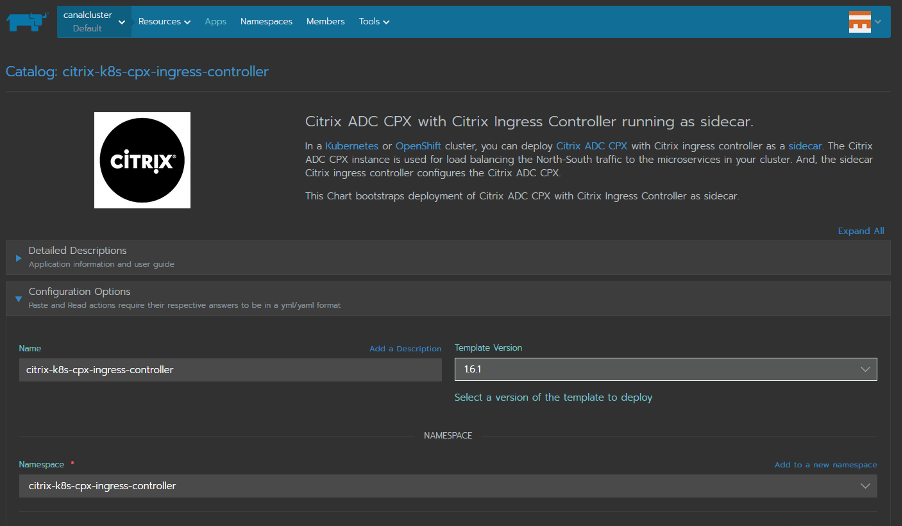
-
Configure the Citrix Ingress Controller settings via the Rancher catalog. These settings are divided into different subsections.
Note: You can find detailed explanation of all the attributes used in these settings here. -
Deployment Settings contain questions about your Kubernetes deployment. License settings contain questions about Citrix Application Delivery Management, which is used as a license server for CPX.
Note: If you don’t provide Citrix Application Delivery Management information during installation, Citrix ADC CPX will come up with the default license.

-
ADC Settings provide a default Non-SNI SSL certificate for the Kubernetes application on Citrix ADC. CIC/CPX Image settings are related to the default Image and Kubernetes Image Pullpolicy.

-
Exporter Settings provide information about citrix-adc-metrics-exporter. This exports ADC metrics to Prometheus, which can be used graphically via Grafana.

-
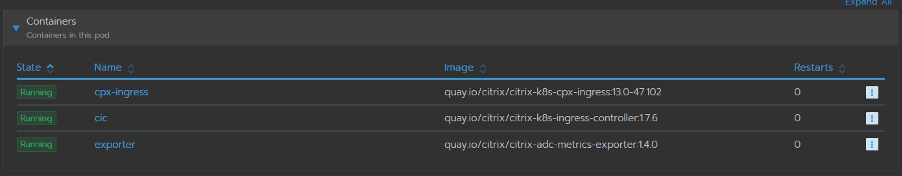
Once you provide all the necessary attributes, you can launch the catalog. This will create a single pod with three containers, Citrix ADC, Citrix Ingress Controller and Citrix ADC Metrix Exporter.
Deploying Citrix Ingress Controller as standalone pod
-
Select citrix-k8s-ingress-controller Rancher catalog for standalone Citrix Ingress Controller.
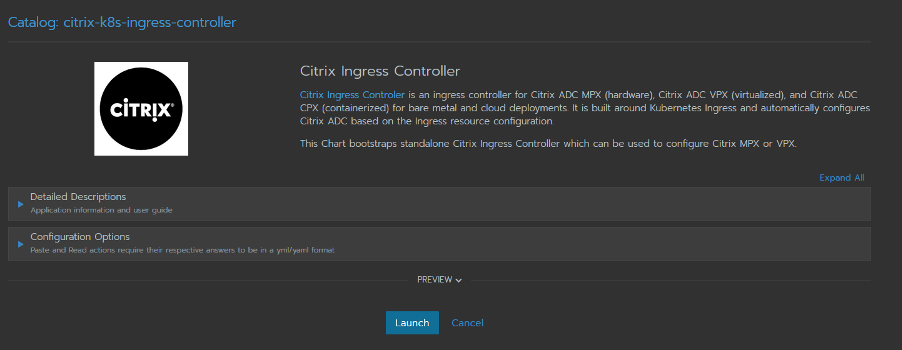
-
The catalog is split into questions similar to the citrix-k8s-cpx-ingress-controller catalog.
-
The Deployment Settings** have a few additional questions compared to the previous catalog.
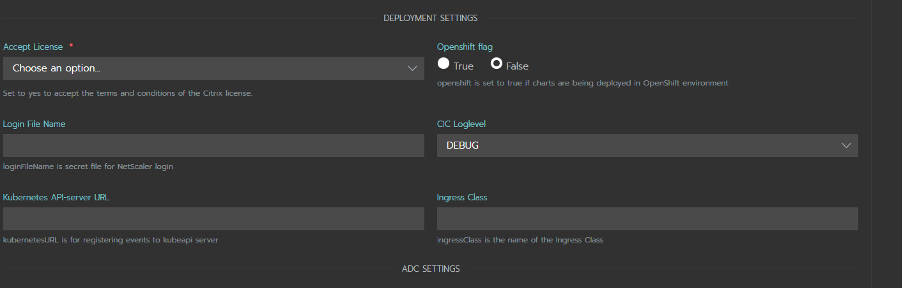
-
Standalone Citrix Ingress Controller is used to configure Citrix ADC, which is outside the Kubernetes cluster. It requires a few more attributes like Citrix ADC IP, Port, Protocol, etc.
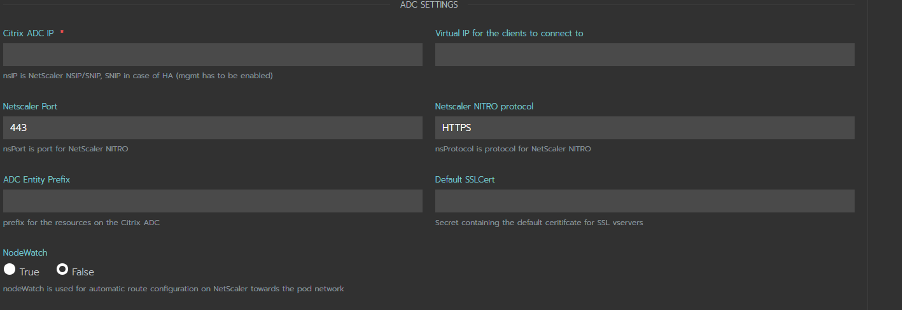
-
Image Settings and Exporter Settings remain the same.
-
Once you launch this catalog, a single pod with Citrix Ingress Controller and Citrix ADC Metric Exporter containers will be up and running.

Deploy a Sample Application from the Rancher UI
Now that we’ve set up Citrix Ingress Controller, we’ll deploy a sample application called guestbook. Here are the Yaml files you’ll need.
-
From the top panel go to Resources > Workloads. Click the Import YAML button.
-
Copy-paste the contents from the YAML file of the sample application as shown below (or see step 3).
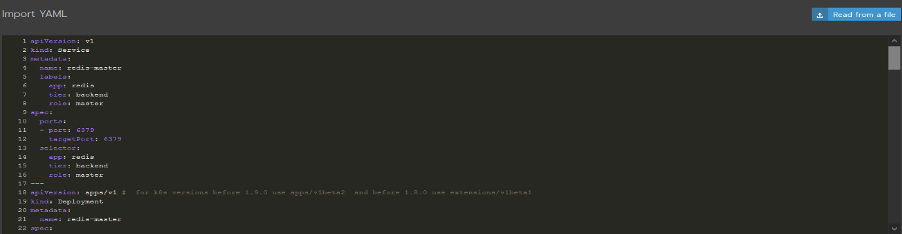
-
Alternatively, you can click on the Read from a file button and provide the sample application link as File name.
-
Sample application guestbook will deploy three services as shown below.
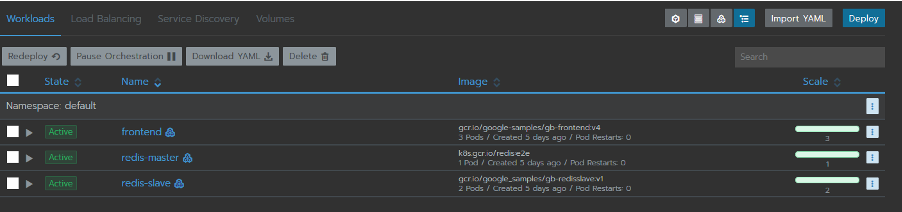
-
We’ll expose the frontend service via the Citrix Ingress Controller.
Configuring Citrix ADC via Citrix Ingress Controller
Set up Citrix ADC CPX running as sidecar with Citrix Ingress Controller
-
Create an ingress rule using the guestbook-ingress.yaml.
-
Once the ingress rule is applied, Citrix Ingress Controller configures the Citrix ADC CPX.
-
View the Citrix ADC CPX configurations via the shell of the Citrix ADC CPX from Resource > Workloads > cpx-ingress
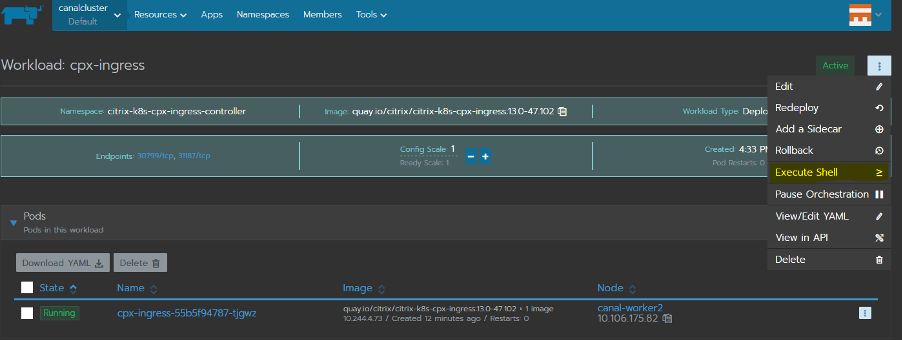
-
Once inside the shell of Citrix ADC CPX, you can view the configuration as shown below.

Set up Citrix ADC VPX/MPX with Citrix Ingress Controller
-
Create an ingress rule using the guestbook-ingress.yaml. This time you’ll need a frontend-ip (VIP). It can either be provided via an annotation called ‘ingress.citrix.com/frontend-ip’ in the ingress YAML (more on annotations) …
-
or it can be provided when the catalog launches.

-
Check your configurations by logging into the VPX.
Steps to Access the application via a Browser
Accessing the application via Citrix ADC CPX
-
Ingress rule for Citrix ADC CPX looks like the image below.
apiVersion: extensions/v1beta1 kind: Ingress metadata: name: guestbook-ingress annotations: kubernetes.io/ingress.class: "citrix" spec: rules: - host: www.guestbook.com http: paths: - path: / backend: serviceName: frontend servicePort: 80 -
To access the application via a browser, you need to send the request to cpx-service.
-
By default, citrix-k8s-cpx-ingress-controller catalog creates the cpx-service as type Nodeport.
Note: You can change the service type to Loadbalancer by editing the service YAML in Rancher UI. -
DNS mapping of NodeIP to hostname has to be added in the hosts file.
Note: The location of hosts file differs based on the Operating System. -
Access the sample application via http://www.guestbook.com:
.
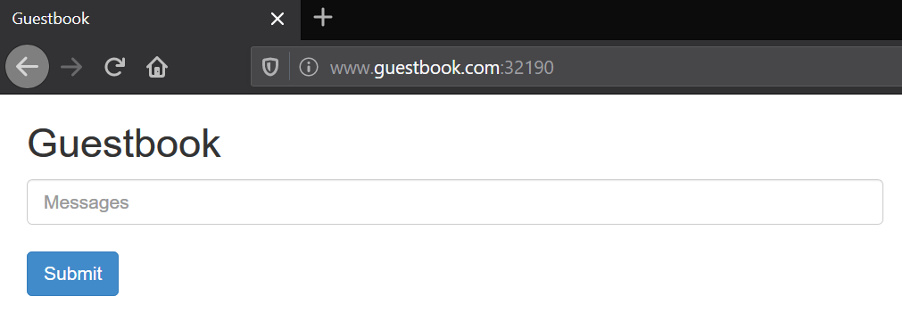
Accessing the application via Citrix ADC VPX
-
Ingress rule for Citrix ADC VPX looks like the image below.
apiVersion: extensions/v1beta1 kind: Ingress metadata: name: guestbook-ingress annotations: kubernetes.io/ingress.class: "citrix" ingress.citrix.com/frontend-ip: “198.51.100.10” spec: rules: - host: www.guestbook.com http: paths: - path: / backend: serviceName: frontend servicePort: 80 -
To access the application via the browser, add a DNS mapping of frontend-ip (VIP) to hostname in the hosts file.
198.51.100.10 www.guestbook.com -
Access the sample application via http://www.guestbook.com:
.
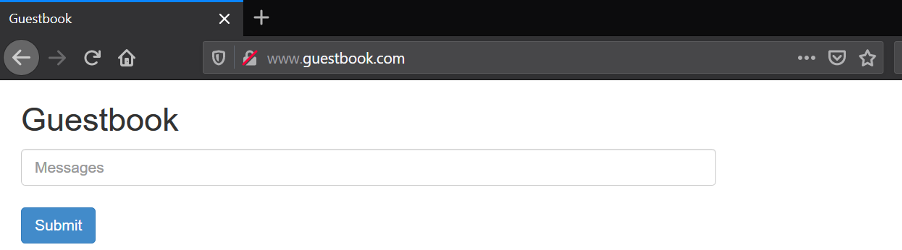
Conclusion
In this article, we’ve shown you how to configure ingress rules using a simple demo. However, Citrix Ingress Controller is capable of much more. It works seamlessly across multiple different deployment modes and platforms and can be used to configure Citrix API gateway.
Using citrix-helm-charts to deploy applications provides a tested, standardized deployment method. With the Rancher catalog UI, Helm charts are even easier to use and configure. With the addition of the citrix-k8s-ingress-controller chart to the Rancher catalog library, you can now access an enterprise-ready load balancer for microservices in a Kubernetes environment.
Related Articles
Apr 18th, 2023