Kubernetes Security: Vulnerability Management
Profile Risk with Vulnerability Management Throughout the Build, Ship, and Run Pipeline
NeuVector scans for vulnerabilities during the entire continuous integration/continuous delivery (CI/CD) pipeline, from Build to Ship to Run. Use the Jenkins plug-in to scan during build, monitor images in registries and run automated tests for security compliance. Prevent deployment of vulnerable images with admission control, but also monitor production containers. Blazing fast, highly scalable image vulnerability analysis scans thousands or hundreds of thousands of images.
NeuVector easily deploys as a container onto virtual machines or bare metal OS environments. The Enforcer container is deployed on each node to protect containers running on it. A Controller container manages the cluster of Enforcers. NeuVector can be managed through the Console, REST API, or CLI.
Full-Lifecycle Security Diagram
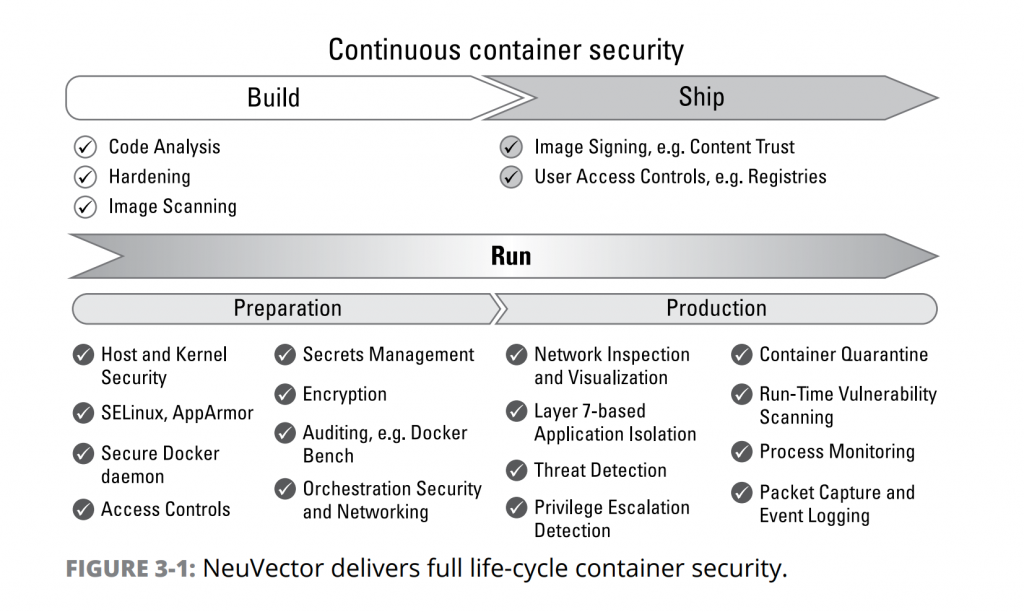
- End-to-End Vulnerability Management: Scanning and admission control during build, test and deployment for supply chain protection
- Run-time Scanning: Scans containers, hosts, and orchestration platforms during run-time to prevent attacks
- CIS Benchmarks: Audits host and container security with Docker Bench and Kubernetes CIS Benchmark for security tests
- Risk Scores and Compliance Reports
NeuVector: Full Lifecycle Cloud Container Security Platform
NeuVector is the only 100% open source, Zero Trust container security platform. Continuously scan throughout the container lifecycle, remove security roadblocks, & bake in security policies at the start to maximize developer agility. Get started by getting NeuVector on GitHub.
Related Articles
Nov 11th, 2024